Teacher: “Okay, James. Can you please write your name on the board?”
James: “Certainly, Miss. However, before I do, may I please ask how you intend to utilise that data?”
That might have sounded ridiculous twenty years ago, but today, everyone is concerned about the safety of their data, both individuals and businesses.
With data breaches happening more often and cyber-attacks becoming more sophisticated, data protection has become a critical priority for companies of all sizes – and someone needs take charge of it.
What data do businesses use?
Relevant information is essential to successfully running a business. Such data may include:
| Customer Data names, contact information, demographics, transactions, online behaviour data | Sales sales by customer, sales by location, revenue, sales volume, products/services, individual purchases/subscriptions, average order value, conversion rates | Marketing customer demographics, website analytics, social media analytics, advertising analytics, market research data |
| Operations data about production, inventory, quality control, supply chain, employees | Processes process cycle times, costs, efficiency, quality (defect rates, error rates, customer satisfaction), degrees of compliance (to regulatory requirements, industry standards, company policies), automation data | Finances revenue, expenses, profit and loss statements, cash flow statement, balance sheets, KPIs, credit card and bank details. |
When collecting and using such data, a business has the responsibility to protect them. Businesses must also ensure they are PCI compliant and adhere to the Privacy Act 1988.
How does an organisation use data?
Data protection is just one aspect of data management, so it’s good to briefly look at this general lifecycle of data:
- Creation/Collection
- Storage & Organisation
- Access & Retrieval
- Processing & Analysis
- Transmission
- Retention or Destruction
Data creation involves obtaining information from your customers, employees, and vendors. After data is collected, you need to organise and store it. For this purpose, databases and data architectures can make it easier to access and retrieve data.
Once data is stored, it can be accessed for processing and/or transmission. With cloud computing and remote work setups, data is often stored in and accessed from multiple locations and devices. This makes it more vulnerable to cyber-attacks and data breaches.
After the data is organised, it needs to be processed and analysed, finding patterns and trends in the data using data analytics tools and techniques. Business decisions can then be made based on the insights gained from this analysis.
In the entire data management process, data protection is crucial to ensuring data security and integrity. An organisation needs to implement measures to protect data from unauthorised access, theft, or loss. Who should handle this?
Who is responsible for data security in your business?
Who is responsible for data security in your business?
The responsibility for protecting business data falls on everyone in the organisation, from the top management to the employees.
- Management: Your CEO, CIO, and CTO should take the lead and set the direction in data protection. They must work in close coordination with the IT department in implementing appropriate security measures and overseeing the data protection strategy.
- Employees: All your staff play a critical part in protecting business data. Everyone must learn and follow best practices for data security. Each employee must be aware of their responsibility and undergo training for it.
- Third-party vendors: If you work with third-party vendors or cloud service providers, ensure that they have proper security measures in place to protect your data.
Each must do their part for data protection strategies to work effectively. Here’s how…
What can be done collaboratively to ensure data safety?
Data protection requires management, employees, and vendors doing each one’s part. Here are some ways to work together in protecting data:
Create a Data Security Policy: Management should have a data security policy that provides guidelines on data access, storage, and disposal, with details on procedures and protocols for handling sensitive data – and make sure they are communicated to all staff and vendors.
Training and Awareness: Management should design a cyber security training program. Employees and vendors should be trained on data security best practices (e.g. creating strong passwords, handling phishing attacks, securing mobile devices).
Access Controls: Access controls should be implemented by management to limit access to sensitive data to only those who need it. This involves setting up user accounts with appropriate permissions and monitoring user activity to detect unauthorised access.
Regular Data Backups: Your IT staff should do regular data backups securely to ensure that critical data can be restored in case of a data loss or breach. They must also test the backups periodically to ensure data integrity.
Vendor Security: Vendors with access to your data should follow the same data security policies and procedures as employees. Conduct background checks on vendors, check their activity, and require them to sign non-disclosure agreements.
Incident Response Plan: Your management should develop an incident response plan. Everyone in the organisation must know how to deal with a data breach, report the incident, mitigate the damage, and notify customers and stakeholders.
Data Protection is a Shared Responsibility
Applications are tools, just like smartphones. A phone’s manufacturer is responsible for making sure the hardware and operating system are running well when you purchase it, but it is the phone owner’s responsibility to use the device safely, maybe use a protective case, download only safe items, use features the way they were designed, and take care of the phone in general.
When storing your data in the Microsoft Cloud, a business remains responsible for the data and data protection. Microsoft is responsible only for the infrastructure (servers, equipment, physical data centres) that stores the data but not the data itself. And while there are some areas where you and Microsoft are jointly responsible, you need to make sure you do your part.
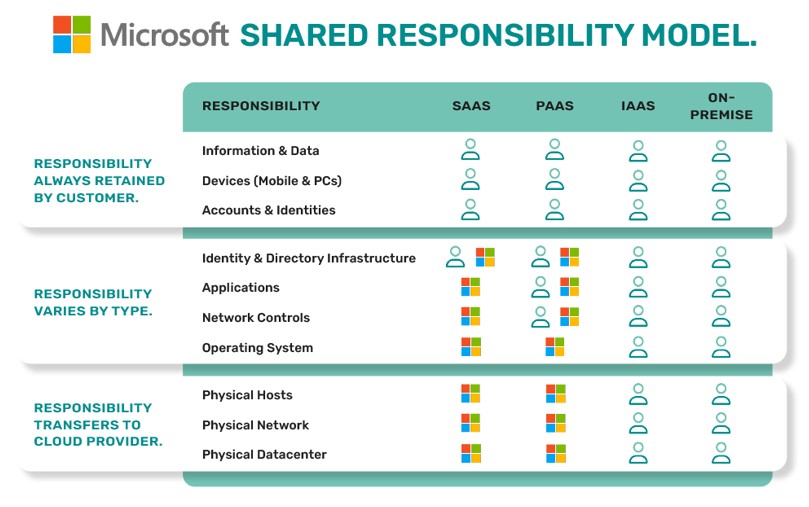
The shared responsibility model put simply means that both Microsoft and its customers have a role to play in keeping data securely protected.
Can’t make sense of the responsibilities? Take a look at the infographic we prepared about Microsoft’s shared responsibility model:
Be proactive: What you can do right now to ensure data protection
Protecting business data is critical if you want to keep your business reputation, be compliant with regulations, and reduce the risk of liabilities and losses. You can be proactive and start with a FREE cyber health check from Lucid IT Solutions.
You may also contact our friendly team of experts if you want more information about data protection.
