Your Complete Business Security Solution.
Download our datasheet to learn more about our cyber security solutions tailored to give you the right protection for your business.
IT Security Solutions.
Secure Data & Resources
We recognise the importance of protecting the confidentiality, accessibility, and integrity of your business systems; therefore, provide tailored IT security solutions.
Each solution has been strategically designed to align with both your current security measures and with those recommended by industry experts. Our powerful tools will highlight any vulnerabilities and potential threats so that they can be resolved before impacting your business.
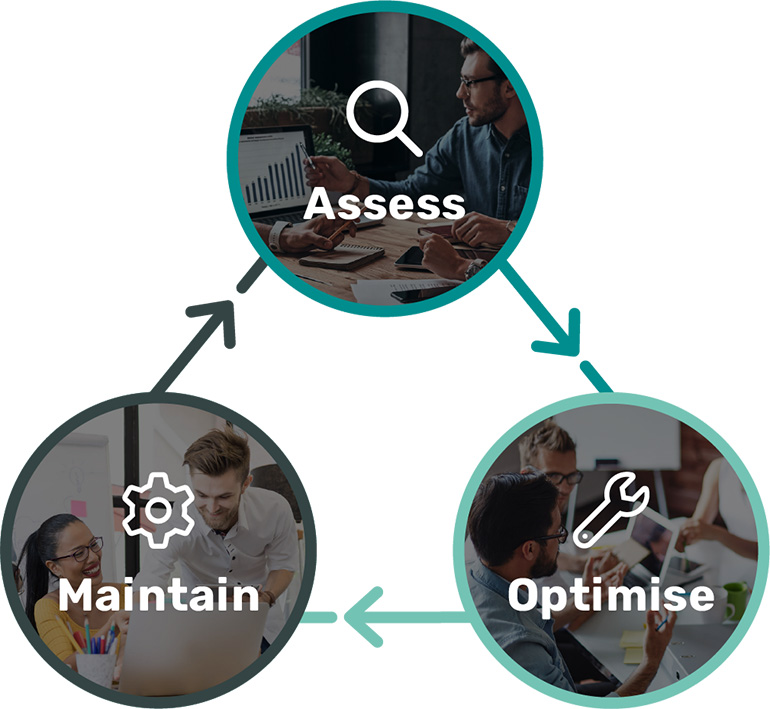
Let us Work Our Magic.
See how we do things
Before delivering a cyber security solution, we assess your current security posture. This will allow us to develop a tailored strategy to optimise your business security.
Once our tools, application settings, and networking configurations are deployed, we’ll manage and maintain the systems to ensure your defences remain strong.
As the threat landscape continues to evolve, this is not a ‘set and forget’ solution. We audit your security on a regular basis to ensure you have the best defence against cyber threats.
ALIGNED WITH THE BEST TO IMPROVE YOUR BUSINESS CYBER RESILIENCE.
We’re fully aligned with the Australian Cyber Security Centre’s (ACSC) cyber security framework for SMEs. This means you’re working with a team of experts who live by the Essential Eight guidelines.
As part of the ASCS’s MSP3 program, IT providers must undergo an assessment to ensure they can implement adequate security, best practices, and secure networks from exposure to malicious cyber-attacks.
As a member, the ACSC will always notify us in advance of any known cybersecurity threats that are yet to be identified to the public. This means we can provide you with proactive security support services that would otherwise be unavailable.
APP CONTROL
Confidently identify the apps, files, and programs your business is running. Restrict the use of unauthorised software with state-of-the-art Application Whitelisting technology.
ADMINISTRATIVE PRIVILEGES
Authorise accounts that require access to your data. Review and remove unauthorised administrative accounts.
MICROSOFT OFFICE MACROS
Protect your systems by reviewing and removing macros, the repetitive series of keyboard and mouse shortcuts, that have not been identified as trusted.
USER APPLICATION HARDENING
Block or remove common software used to download or run malicious software, preventing it from running on your computer systems.
PATCH APPLICATIONS
Modify and update your programs to improve their security performance and mitigate known security vulnerabilities.
OPERATING SYSTEMS
Apply the latest security updates to your computer’s operating system to prevent cybercriminals from attacking your network.
MULTI-FACTOR AUTHENTICATION
Add an extra layer of security, assure a user’s identity, and better control who has access to your files by enabling MFA.
DAILY BACKUPS
Prepare while you’re ahead by performing daily backups on your files, applications, devices, and servers.
Free eBook: Beginners Guide to the Essential 8.
With cybercrime on the rise, you must ensure your business has a strong cyber security posture. But we understand it can be hard just getting started. That’s why we’ve put together this beginners guide based on the Australian Cyber Security Centre’s Essential 8. We cut out the tech-jargon and share quick wins to help you get on track.
PROTECTION LIKE NEVER Before.
Your Continuous Cycle of Improvement
Before creating a cybersecurity strategy, it is imperative to spend time understanding any holes you may have in current processes.
Our experienced technicians will run a full IT security audit on your existing infrastructure to determine strengths and weaknesses, along with the cyber defences that your business would benefit from. Audits are available to companies of all scales in an array of different industries.
Microsoft Defender Vulnerability Management.
Discover, Assess & Remediate Vulnerabilities and Misconfigurations All in One Place
Defend against cyberthreats
Activate Microsoft Defender for Office 365 to help guard against viruses, spam, unsafe attachments, suspicious links, and phishing attacks.
Manage mobile devices, tablets, and computers
Apply security policies to help protect work data on company-owned and employee devices. Keep company data within approved apps. Remove business data from lost or stolen devices with Microsoft Intune.
Enable secure remote access and protect identity
Help employees securely access business apps wherever they work with conditional access. Safeguard against password loss or theft with advanced multifactor authentication.
Help protect business data
Encrypt sensitive emails and restrict copying and forwarding of confidential business information with Azure Information Protection. Enable unlimited cloud archiving.
Enterprise-grade endpoint security with Microsoft Defender for Business
Get protection against sophisticated ransomware attacks across devices—Windows, macOS, Android, and iOS4—with next-generation antivirus, endpoint detection and response.
Learn More About Microsoft 365 Business Premium.
Zero Trust Security.
Trust What You Know.
Protect Against What You Don’t.
Developing and maintaining your business’s strong cyber security stance is our top priority. To ensure full protection, we work with leading technology from ThreatLocker. This allows us to audit your network, work out what you use and “trust” it. If we don’t know it, we don’t let it run.
Our state-of-the-art tech is a critical line of defence in your cyber security, letting you track and control internal and external data access and mitigating the risk of data theft.
Cybersecurity Awareness Training.
More than 50% of all security breaches are caused internally.
Why? Because hackers have become more advanced than ever. They have perfected methods of targeting and manipulating your staff into clicking links and opening files that are contaminated with malicious software.
Our security awareness training helps bridge the knowledge gap and provides staff with the necessary tools to identify such attacks. By completing cybersecurity training, you are effectively giving your business the greatest defence against external unauthorised access to your systems.
SECURITY TRANSFORMATION IN Action.
Beach Avenue Wholesalers
Our team of cyber security experts are dedicated to helping each and every one of our clients feel safe and protected against cybercrime.
Check out how we were able to successfully transform Beach Avenue Wholesalers’ cyber security stance.
PROTECTING YOUR BUSINESS STARTS HERE.
When it comes to your cyber security, there’s no time like the present to start filling in the missing gaps and reducing your business’s vulnerabilities.
